 Sabtu, 31 Mei 2025 (23:40)
Sabtu, 31 Mei 2025 (23:40)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Cryptography Part 14: Key Schedule and g( ) function in AES (Tech Lover) View |
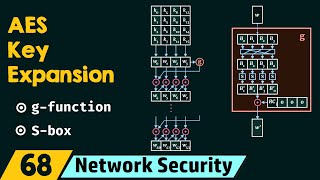 |
AES Key Expansion (Neso Academy) View |
 |
Key Expansion in AES | Round Constant and g function in Key Expansion in AES (Chirag Bhalodia) View |
 |
Applied Cryptography: AES - Part 13 (Leandro Junes) View |
 |
Advanced AES Using Dynamic Key (Nishant Pal) View |
 |
AES key Expansion (Dr. Moonther) View |
 |
Automatic Search of Attacks on Round-Reduced AES and Applications (Crypto 2011) (IACR) View |
 |
Improved Key Recovery Attacks on Reduced Round AES with Practical Data and Memory Complexities (IACR) View |
 |
8 Diffie-Hellman Key Exchange (DHKE) Algorithm (Dr Nitin Naik - Aston University, UK) View |
 |
AES Example | AES Encryption Example | AES Example Solution | How to solve AES example (Chirag Bhalodia) View |