 Kamis, 29 Mei 2025 (03:12)
Kamis, 29 Mei 2025 (03:12)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Authentication u0026 Secure Communication for IoT Devices (RenesasPresents) View |
 |
Secure Key Storage for IoT Devices (Sectigo) View |
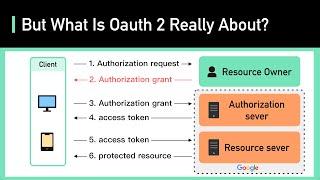 |
OAuth 2 Explained In Simple Terms (ByteByteGo) View |
 |
oAuth for Beginners - How oauth authentication🔒 works (IT k Funde) View |
 |
SSL, TLS, HTTPS Explained (ByteByteGo) View |
 |
The CSIAC Podcast - Authenticating Devices in Fog Multi-Access Computing Environments (CSIAC) View |
 |
Threat Landscape and Protective Strategies for IoT and LSMAS (Monisha J) View |
 |
Microsoft Entra ID Beginner's Tutorial (Azure Active Directory) (Microsoft Mechanics) View |
 |
Blockchain In 7 Minutes | What Is Blockchain | Blockchain Explained|How Blockchain Works|Simplilearn (Simplilearn) View |
 |
IoT- Based Smart Utility Meter- American University of Sharjah (Mais Haj Hassan) View |