 Kamis, 29 Mei 2025 (11:53)
Kamis, 29 Mei 2025 (11:53)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
YARA for PE Analysis (NYUCyFor) View |
 |
YARA: The Malware Detection Tool You Need to Know (Guided Hacking) View |
 |
What are Yara Rules (and How Cybersecurity Analysts Use Them) (Simply Cyber - Gerald Auger, PhD) View |
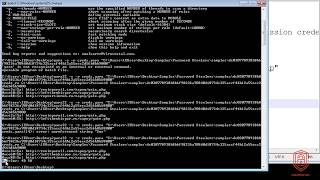 |
Malware Analysis Bootcamp - Creating YARA Rules (HackerSploit) View |
 |
Create YARA rules with GHIDRA | MALWARE Analysis of Havoc Demon implants (Jai Minton - CyberRaiju) View |
 |
How To Write a YARA Rule That Can Find Binaries That Have More Than 3 URLs (Mossé Cyber Security Institute) View |
 |
Using Disassembled Code to Create Yara Rules! (Dr Josh Stroschein - The Cyber Yeti) View |
 |
Using Yara for Detecting Bloated Overlays (Dr Josh Stroschein - The Cyber Yeti) View |
 |
Using YARA to identify and classify malware samples (Mossé Cyber Security Institute) View |
 |
Learn to create Yara Rules for malware classification and to scan malware Files (PBER ACADEMY) View |