 Sabtu, 18 Januari 2025 (16:32)
Sabtu, 18 Januari 2025 (16:32)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Creating a Cyber Attack Part 5 (Post Exploitation - with BeeF) (2code monte) View |
 |
Creating a Cyber Attack – Part 4 (Exploiting - Getting Access ) (2code monte) View |
 |
Cross-Site Request Forgery Demonstrated! (Loi Liang Yang) View |
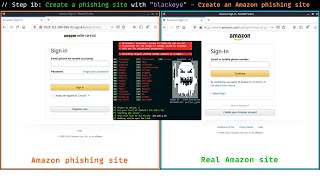 |
Create a phishing site in 4 minutes | Suprisingly easy and convenient (Cyber Iota) View |
 |
i HACKED my wife’s web browser (it’s SCARY easy!!) (NetworkChuck) View |
 |
I’m not sorry (Ray William Johnson) View |
 |
Cross-Site Scripting (XSS) Explained And Demonstrated By A Pro Hacker! (Loi Liang Yang) View |
 |
hacking every device on local networks - bettercap tutorial (Linux) (Nour's tech talk) View |
![Download Lagu Take Control of Web Browsers with BeEF [Tutorial] Thumbnail](https://img.youtube.com/vi/EL96fXFNLNA/mqdefault.jpg) |
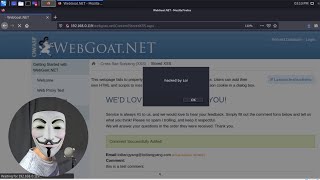
Take Control of Web Browsers with BeEF [Tutorial] (Null Byte) View |
 |
I Stole a Microsoft 365 Account. Here's How. (John Hammond) View |