 Rabu, 16 April 2025 (18:51)
Rabu, 16 April 2025 (18:51)
 Music |
 Video |
 Movies |
 Chart |
 Show |
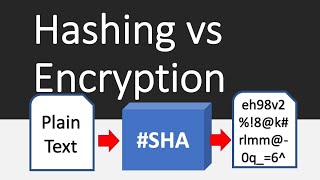 |
Hashing vs Encryption Differences (Programming w/ Professor Sluiter) View |
 |
Hashing Algorithms and Security - Computerphile (Computerphile) View |
 |
Password Storage Tier List: encryption, hashing, salting, bcrypt, and beyond (Studying With Alex) View |
 |
Difference Between Encryption vs Encoding vs Hashing vs Obfuscation Explained (Learn with Whiteboard) View |
 |
Hashing and Digital Signatures - CompTIA Security+ SY0-701 - 1.4 (Professor Messer) View |
 |
Hashing vs Encryption Explained in 5 Minutes (Vinsloev Academy) View |
 |
What is a Cryptographic Hashing Function (Example + Purpose) (Whiteboard Crypto) View |
 |
SC-900 EP 07: Encryption, Hashing u0026 Signing (A Guide To Cloud) View |
 |
Hash Password and assign User role in .NET 8 | User management in .NET | Part 17 (Let's Program) View |
 |
Encryption or Hashing: Making the Right Decision (Good Morning Developers) View |