 Kamis, 9 Januari 2025 (02:37)
Kamis, 9 Januari 2025 (02:37)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
How to exploit a buffer overflow vulnerability - Theory (Daniel Slater) View |
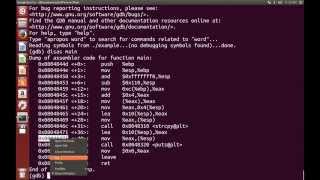 |
How to exploit a buffer overflow vulnerability - Practical (Daniel Slater) View |
 |
How to exploit a buffer overflow vulnerability | Full Practical (LinuxSploit) View |
 |
how do hackers exploit buffers that are too small (Low Level) View |
 |
Buffer Overflow attack - Exploitation and Theory of Vulnerability (Be Cool IT) View |
 |
What is a Stack Buffer Overflow Exploring How To Exploit the Stack (Dr Josh Stroschein - The Cyber Yeti) View |
 |
How They Hack: Buffer Overflow u0026 GDB Analysis - James Lyne (James Lyne) View |
 |
Buffer Overflow 101: Ep 1 - x86 Memory Fundamentals (flipthebit) View |
 |
Buffer Over Flow Explained and Simplified P6 - Theory (Motasem Hamdan | Cyber Security \u0026 Tech) View |
 |
Practical exploitation of a Buffer Overflow vulnerable C program (Engineer Man) View |