 Sabtu, 15 Maret 2025 (12:14)
Sabtu, 15 Maret 2025 (12:14)
 Music |
 Video |
 Movies |
 Chart |
 Show |
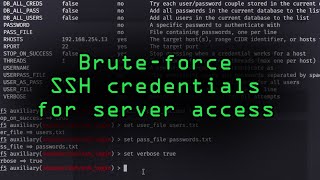 |
How Hackers Could Brute-Force SSH Credentials to Gain Access to Servers (Null Byte) View |
 |
How to exploit SSH with Metsaploit | Kali Linux (SecureWithAashir) View |
 |
this SSH exploit is absolutely wild (Low Level) View |
 |
How to SSH Without a Password (like a boss) (Tony Teaches Tech) View |
 |
SSH Honeypot in 4 Minutes - Trap Hackers in Your Server (Wolfgang's Channel) View |
 |
how to exploit Metasploitable 2 ssh port: 22 (Hackersio) View |
![Download Lagu Haunt a Computer Using SSH [Tutorial] Thumbnail](https://img.youtube.com/vi/M0eEwqUpKDc/mqdefault.jpg) |
Haunt a Computer Using SSH [Tutorial] (Null Byte) View |
 |
Hackers can SSH in Your Linux (DO THIS NOW TO SECURE SSH!!!) (HackHunt) View |
 |
How SSH Works (Mental Outlaw) View |
 |
How To Hack and Exploit Port 22 SSH Metasploitable 2 - Home Hacking Lab Video 6 (InfoSec Pat) View |