 Minggu, 11 Mei 2025 (02:48)
Minggu, 11 Mei 2025 (02:48)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Kubernetes Security Fundamentals: Authentication - Part 2 (Datadog) View |
 |
Kubernetes Security Fundamentals: API Security - Part 2 (Datadog) View |
 |
Kubernetes Security | Authentication Pt1 (JMMTechnology) View |
 |
Kubernetes Security | Authenticating Webhook and Authentication Proxy Explained (JMMTechnology) View |
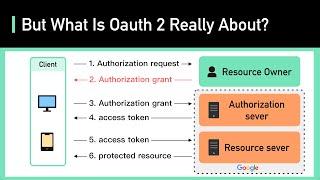 |
OAuth 2 Explained In Simple Terms (ByteByteGo) View |
 |
Lightning Talk: Beyond Basic Authentication - Leveraging OIDC to Secure Kubernetes Clusters (CNCF [Cloud Native Computing Foundation]) View |
 |
Remote Authentication Explained: Security Implementation for DevSecOps Teams | Kubernetes Course (Practical DevSecOps) View |
 |
How to protect your APIs against these 6 security threats (Google Cloud Tech) View |
 |
AKS (Azure Kubernetes Service) Security u0026 Identity updates | Ignite 18 (Microsoft Mechanics) View |
 |
AZ-900 Episode 27 | Azure Key Vault | Secret, Key and Certificate Management (Adam Marczak - Azure for Everyone) View |