 Rabu, 21 Mei 2025 (14:54)
Rabu, 21 Mei 2025 (14:54)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Perimiter Network Access Model vs ZeroTrust Access Model (LegaSystems) View |
 |
What is Zero Trust Network Access (ZTNA) The Zero Trust Model, Framework and Technologies Explained (The CISO Perspective) View |
 |
Software Defined Perimeter vs. Zero Trust Access (Jason Maynard) View |
 |
How does zero trust work I Lightboard Techtalk (Progress Kemp) View |
 |
What is Security Service Edge (SSE) SASE vs SSE vs VPN (The CISO Perspective) View |
 |
Software Defined Perimeter (SDP) Accelerates Zero Trust Strategy (TechTransformation) View |
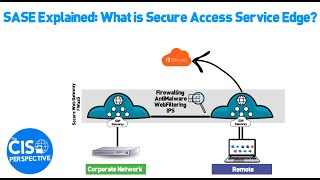 |
What is Secure Access Service Edge (SASE) (The CISO Perspective) View |
 |
ZONEZERO® Perimeter Access Orchestration (Safe-T Data) View |
 |
Perimeter 81 ZTNA Review: The Ultimate Zero-Trust Network Access Solution for Enterprises (UK Pro Reviewer) View |
 |
Top Cybersecurity Expert Reveals Best Zero Trust Techniques for 2025 (FuturisticGeeks) View |