 Jumat, 14 Maret 2025 (12:22)
Jumat, 14 Maret 2025 (12:22)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Phishing attacks are SCARY easy to do!! (let me show you!) // FREE Security+ // EP 2 (NetworkChuck) View |
 |
Ethical Hacking Basics: Crafting the Perfect Phishing Attack with the Social Engineering Toolkit (JRob Cyber) View |
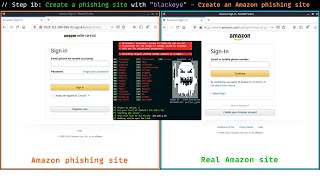 |
Create a phishing site in 4 minutes | Suprisingly easy and convenient (Cyber Iota) View |
 |
Kali Linux Social Engineering Tookit (setoolkit) Web Credential Harvester Attack Demo (Alaam Amershi) View |
 |
I Stole a Microsoft 365 Account. Here's How. (John Hammond) View |
 |
1 Phishing with SET (CyberPro Tec) View |
 |
Phishing with SET (CyberPro Tec) View |
 |
Phishing and Spoofing using SET (William Graham) View |
![Download Lagu [Tutorial] Basic phishing with S.E.T. Thumbnail](https://img.youtube.com/vi/Yh-oUzqKY1A/mqdefault.jpg) |
[Tutorial] Basic phishing with S.E.T. (DarkSoloNetwork) View |
 |
Phishing With SET (TheCyberCare) View |