 Senin, 24 Februari 2025 (13:25)
Senin, 24 Februari 2025 (13:25)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Responsibility for the Harm and Risk of Software Security Flaws 1 3 (All Hacking Cons) View |
 |
OWASP AppSec 2010: Responsibility for the Harm and Risk of Software Security Flaws 1/3 (Christiaan008) View |
 |
Cybersecurity Assurance Chapter 3 Part 1 - Determining Information Security Risk (Rutgers Accounting Web) View |
 |
Risk Management MindMap (3 of 3) | CISSP Domain 1 (Destination Certification) View |
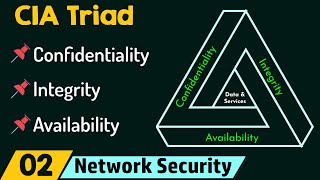 |
CIA Triad (Neso Academy) View |
 |
Module 3 Part 1 (Introduction to Information Security – I) View |
 |
Intro To Cyber: Security Management 7-1 (Mnemosyne) View |
 |
Episode 2 - Security Concepts: Threat, Vulnerability, Risk, Threat Agent u0026 Countermeasure (Learning Security With Mayur) View |
 |
Intro Cyber 1-3 (Mnemosyne) View |
 |
RHIT Exam Prep 043 | Cybersecurity | 💻🎀📚 (Professional Certifications) View |