 Jumat, 7 Februari 2025 (10:41)
Jumat, 7 Februari 2025 (10:41)
 Music |
 Video |
 Movies |
 Chart |
 Show |
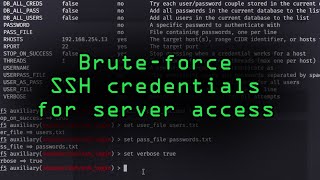 |
How Hackers Could Brute-Force SSH Credentials to Gain Access to Servers (Null Byte) View |
 |
How to exploit SSH with Metsaploit | Kali Linux (SecureWithAashir) View |
 |
How SSH Works (Mental Outlaw) View |
 |
this SSH exploit is absolutely wild (Low Level) View |
 |
How a Hacker Saved The Internet (fern) View |
![Download Lagu Haunt a Computer Using SSH [Tutorial] Thumbnail](https://img.youtube.com/vi/M0eEwqUpKDc/mqdefault.jpg) |
Haunt a Computer Using SSH [Tutorial] (Null Byte) View |
 |
how to exploit Metasploitable 2 ssh port: 22 (Hackersio) View |
 |
Linux got wrecked by backdoor attack (Fireship) View |
 |
50 Attacking SSH - Bruteforce Attack (TechAcdnt) View |
 |
SSH IP Spoofing Attack on Tor (Sam Bent) View |